Keep “Claims aware” and click “Start“
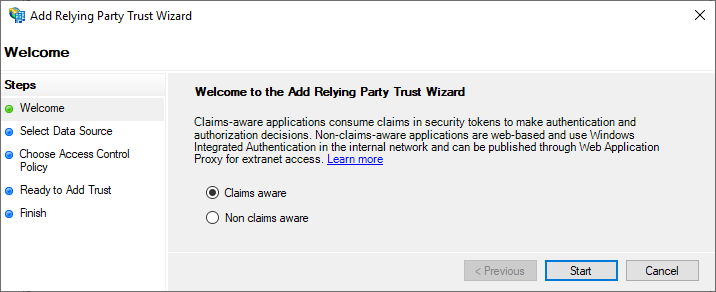
Select “Import data about the relying party for a file“, click “Browse” and select the metadata file downloaded from your Workspace ONE Access or your Unified Access Gateway
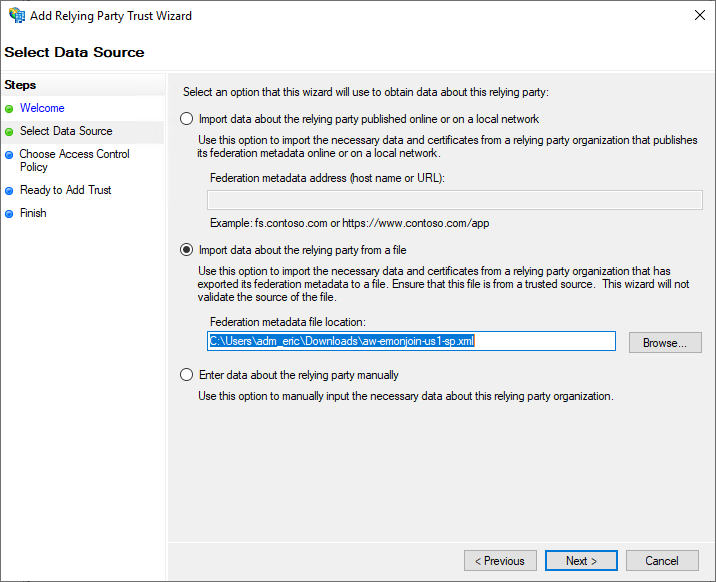
Specify a “Display name”
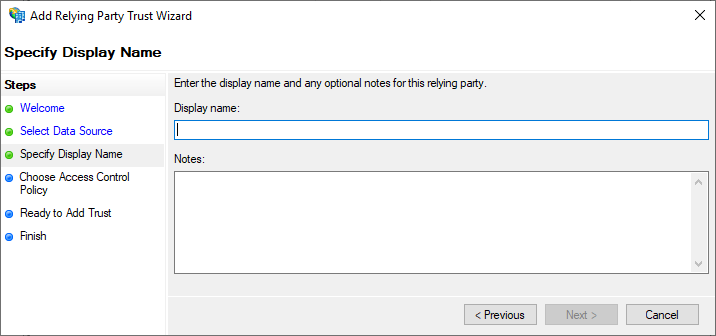
Select “Permit everyone“
Click “Next“
Click “Close“
Click “Edit Claim Issuance Policy…“
Click “Add Rule“
Ok now we have a difference between UAG and Workspace ONE Access
For Workspace ONE Access :
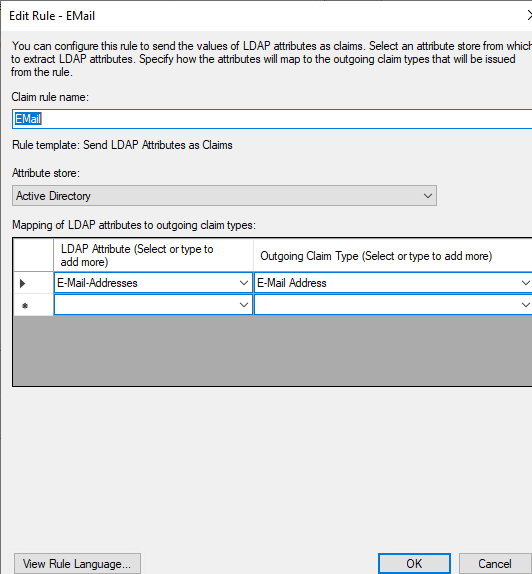
We need to create 2 rules, the first one consist to the email address..
Select “Send LDAP Attributes as Claims“
In Attribute store, select : “Active Directory” and the following Attributes/Outgoing Claim Type :
LDAP Attribute : “E-Mail-Addresses“
Outgoing Claim Type : “E-Mail Address“
And the second one consist to transform the output to something readable for Workspace One Access:
Select “Send Claims Using a Custom Rule“
In “Claim rule name:“, type your rule name eg : “Transform“
In “Custom rule“, copy and past the following line but change the “https://my_tenant.vmwareidentity.eu” by your tenant fqdn
c:[Type == "http://schemas.xmlsoap.org/ws/2005/05/identity/claims/emailaddress"]
=> issue(Type = "http://schemas.xmlsoap.org/ws/2005/05/identity/claims/nameidentifier", Issuer = c.Issuer, OriginalIssuer = c.OriginalIssuer, Value = c.Value, ValueType = c.ValueType, Properties["http://schemas.xmlsoap.org/ws/2005/05/identity/claimproperties/format"] = "urn:oasis:names:tc:SAML:1.1:nameid-format:emailAddress", Properties["http://schemas.xmlsoap.org/ws/2005/05/identity/claimproperties/spnamequalifier"] = "{https://my_tenant.vmwareidentity.eu}");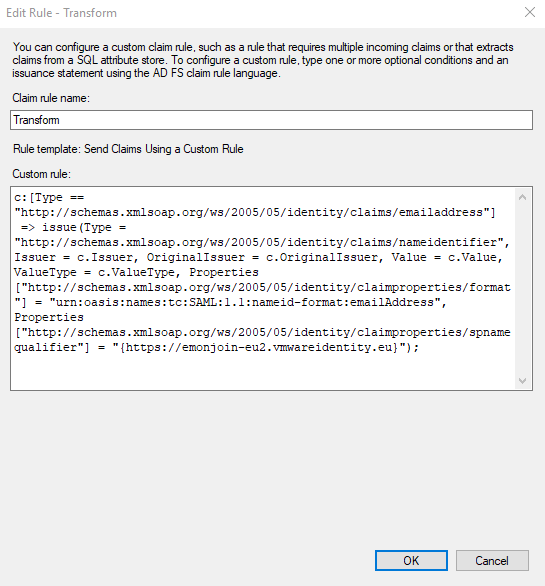
For Unified Access Gateway:
It’s more simple,
Give a Claim rule name : eg. “Get UPN“
Select “Send LDAP Attributes as Claims“
In Attribute store, select : “Active Directory” and the following Attributes/Outgoing Claim Type :
LDAP Attribute : “User-Principal-Name“
Outgoing Claim Type : “Name ID“
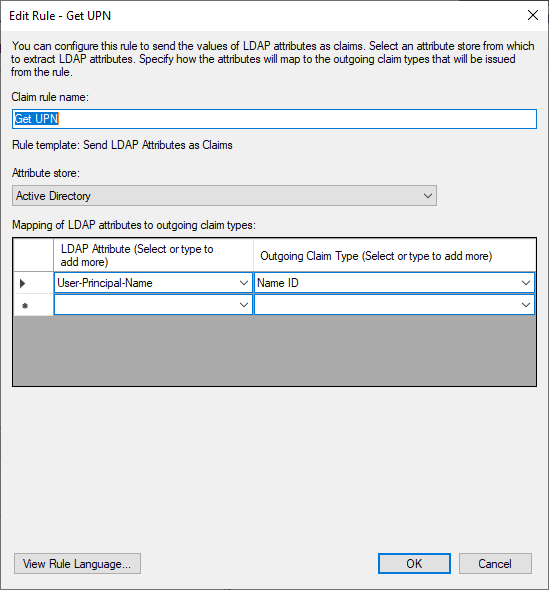
Click “Finish“
Click “Apply“



Recent Comments