Horizon Suite 2212 is GA since last week and of course I already upgraded all my lab with this new release.
I was particularly interested by the Application on Demand so directly manage App Volumes application on RDS with all entitlement done within the Horizon Console.
The principle consist of adding App Volumes server in Horizon and then assign it to an “Automated” farm.
Now when you add you App Volumes Server into Horizon, you’ll certainly need to import App Volumes certificates into the “Trusted Root Certification Authorities” folder and then restart Horizon Services on all you Connection Servers.
Now even if doing that, you can encounter the following issue, with Enterprise signed certificate :
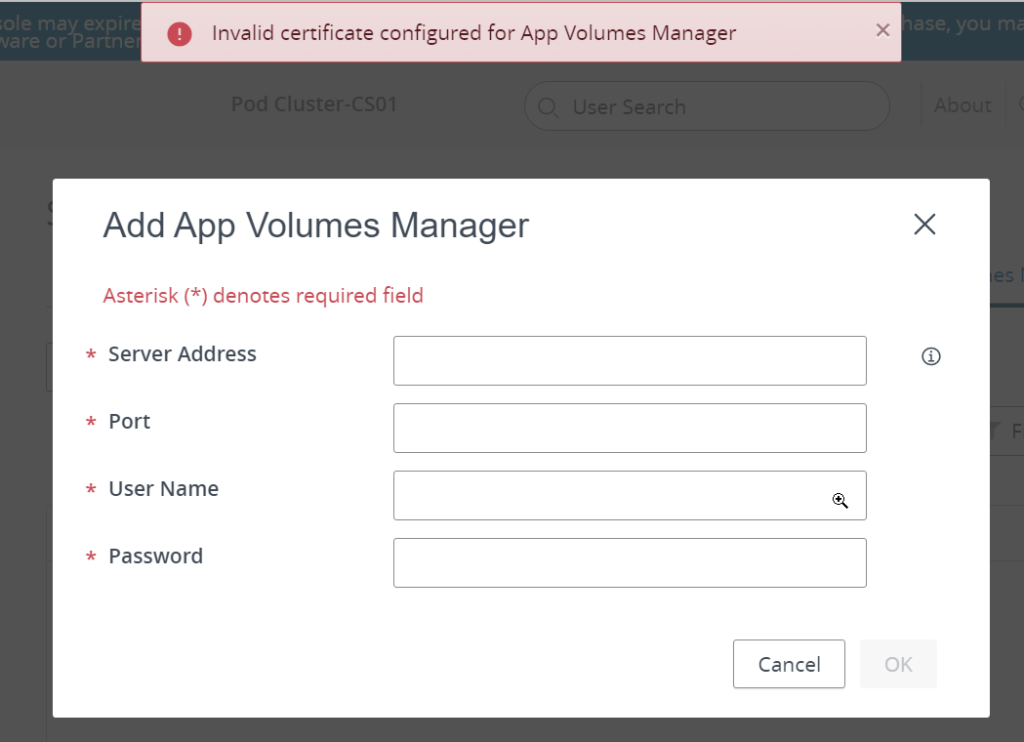
I had this issue on my lab, so to get it solved, I had to generate a new certificate for my App Volumes server using a new Template.
This is how to do it ….
Open the Certification Authority mmc console, select Certificate Templates then Manage
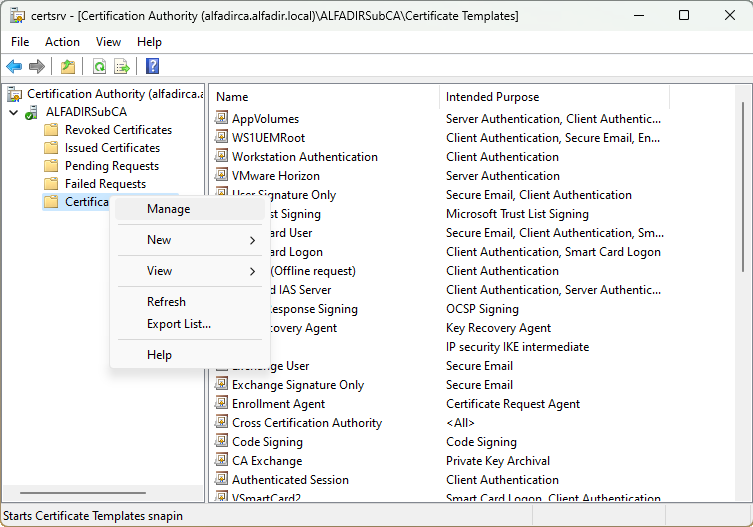
Select “Web Server” then Duplicate Template
Use following settings :
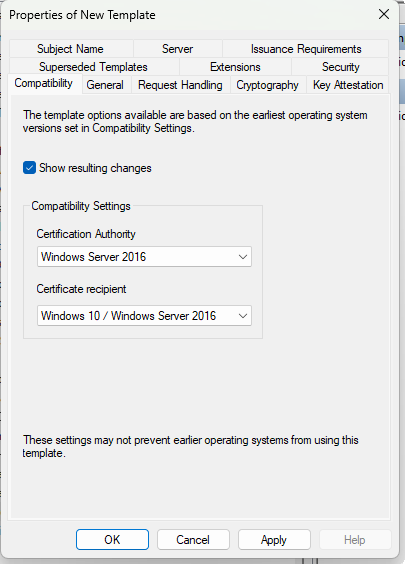
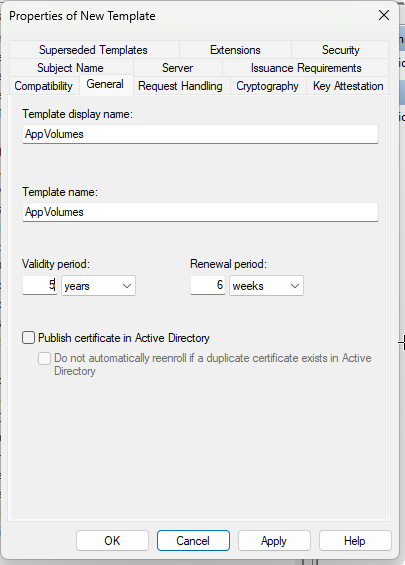
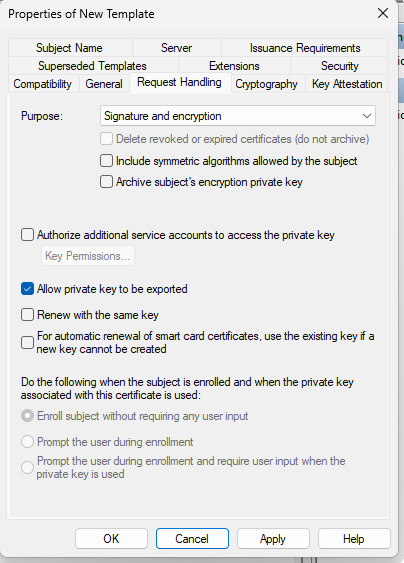
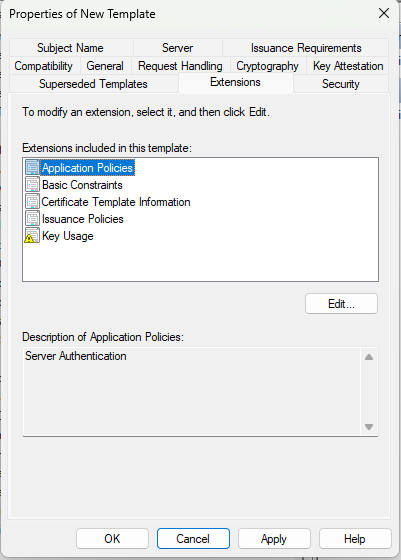
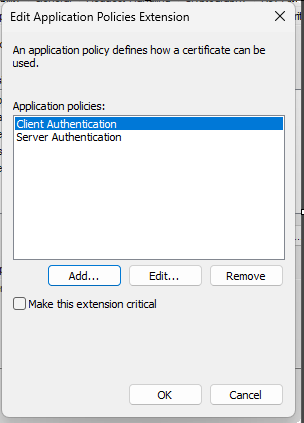
This setting is very important because it’s the cause of the problem. You need both Client Authentication and Server Authentication (see : https://kb.vmware.com/s/article/2095969)
All others are defaults
Once the new template is created, we need to make it “usable” : click “New” then “Certificate Template to Issue”
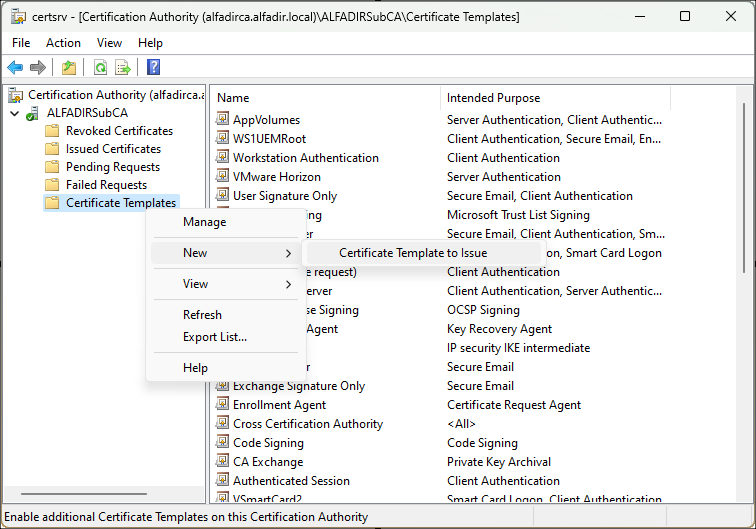
And select the new Template :
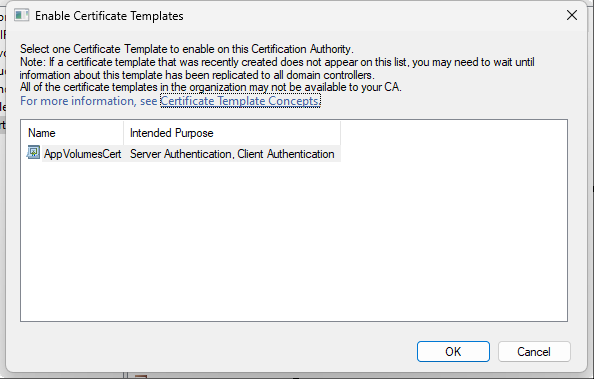
You can new generate a new certificate :
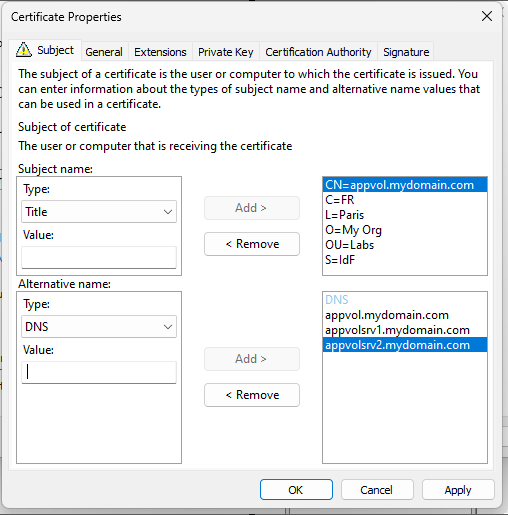
Once you new certificate generated, you can export it as pfx and then convert it to PEM + Key using the OpenSSL
#openssl.exe pkcs12 -in av-cert.pfx -nocerts -out av-cert.key.pem -nodes -password pass:<password>
#openssl.exe pkcs12 -in av-cert.pfx -nokeys -out av-cert.pem -password pass:<password>
#openssl.exe rsa -in av-cert.key.pem -out av-cert.key
# del av-cert.key.pemNext step, edit nginx.conf file (in c:\Program Files (x86)\Cloud Volumes\Manager\nginx\conf), and change the certificate and key name as required.
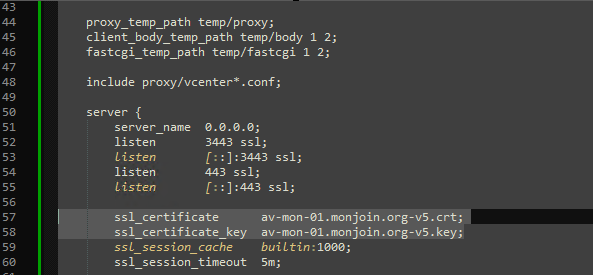
Copy the certificate (but not the private key) to your Connections Servers and install it into the “Trusted Root Certification Authorities” store:



Recent Comments