I’ll not talk about the configuration of AD FS itself but how to create the relying party for both Workspace ONE Access and UAG… spoiler: the configuration is not the same 🙂
So here the common part who consist to the creation of the Relying Party Trusts:
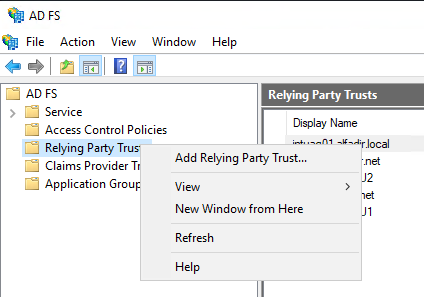
Open you AD FS Manager, select “Relying Party Truts” and with the select “Add Relying Party Trust…“
Pages: 1 2



Recent Comments