Recently I had to work on a project that imply Shibboleth as IdP (Identity Provider), so you will see below how to configure it in Workspace One Access as a 3rd party IdP.
One of the major issue with Shibboleth (in my case) is it only provides a samAccountName but not a UserPrincipalName (upn), so basically the User name without the domain name (eg. e.monjoin but not e.monjoin@mydomain.dom). It works in many situation excepted in a multi domain configuration where you can potentially have the same username in two different domain and you have a trust relationship between them (eg. e.monjoin@finance.domain.com and e.monjoin@technical.domain.com). In this case WS1 Access will not be able to choose a account you will see the following error :
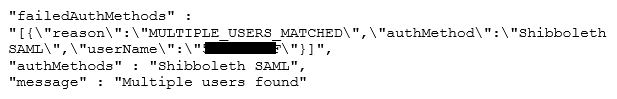



Recent Comments