I recently had to upgrade a Horizon infrastructure with around 180 pools and different masters, as you can imagine, that could be exhausting first to check which master is in use and what’s the current snapshot as well, so after searching a little bit on the Net, I’ve able to find what I need :
Continue reading…Tagged: VMware
ADFS with VMware Unified Access Gateway (UAG)
This article talks about configuration of ADFS with VMware Unified Access Gateway without the use of Workspace One Access.
There’re two use cases here to configure ADFS with Unified Access Gateway
- Use Case #1: ADFS as MFA, so users first authenticate using ADFS, and then authenticate using standard credential to get the list of available resources (desktop or apps)
- Use Case #2: ADFS for single authentication method, so users will authenticate once with ADFS and then will connect to VDI VMs or published apps without the need to enter any other credentials. This use case of course required VMware TrueSSO to works
Initial configuration is the same for both and to make it short here the different steps required:
- Change Expiration Period for Service Provider Metadata
- Deploy UAG
- Configure Edge Service and specify a Connection Server fqdn (not the load-balancer)
- Check connection is working
- Connect to <federation fqdn> and save the FederationMetadata.xml file
- Import FederationMetadata.xml in UAG (Upload Identity Provider Metadata)
- Configure UAG for SAML or SAML and Passthrough auth methods
- Specify Identity Provider
- Download SAML Service Provided .xml file
- Configure ADFS
- Add a new Relying Party Trusts
- Specify UAG SP .xml file as source
- Configure Claim Issuance Policy
- Connect to UAG as “client”
- Auth using ADFS
- Auth using AD credential
Now if we want to go further and implement ADFS with TrueSSO:
- Generate SAML IdP Settings
- Import signed cert or use Generated one
- Copy Content of Download IDP Settings
- Configure Horizon Connect Server for SAML auth with UAG and ADFS
- Connect to admin console of Horizon Connection Server
- Add SAML Authenticator for UAG
- Mode Static
- Past Content of UAG Download IDP Settings
- Change EntityId if required
- Add SAML Authenticator for ADFS
- Mode Static
- Past Content of FederationMetadata.xml
- Enable TrueSSO for UAG and ADFS
- Using vdmUtil, enable both authenticator
- Check True SSO connection
- Connect to UAG as Client
- Once authenticated to ADFS, the list of available resource appears, and you can login without any other cred
That said, let see with some nice pictures how we do that :
Continue reading…New Horizon Cloud Connector v1.10.0
What’s New March 25, 2021 (v2103, v1.10, v21.03, v21.1)
- Horizon Cloud Administration Console is now Horizon Universal Console.
- Universal Broker and multi-cloud assignments are now available for existing deployments of Horizon Cloud pods on Microsoft Azure. Universal Broker provides a single URL for end-users to access virtual desktops and apps, whether on-premises or in the cloud, as well as multi-cloud assignments that enable you to create dedicated and floating virtual desktop assignments that span multiple pods and sites.
- Universal Broker and multi-cloud assignments now support Horizon pods on Azure VMware Solutions (AVS), enabling unified brokering of multi-cloud assignments across hybrid and multi-cloud deployments, supporting both Horizon pods and Horizon Cloud pods on Microsoft Azure.
- App Volumes for Horizon Cloud pods on Microsoft Azure now supports Windows 10 Enterprise multi-session, allowing multiple users to each login into individual sessions with their own app assignments. App Volumes and MSIX app attach formats can be delivered to a session simultaneously, and the App Volumes agent will use the correct mode of virtualization for each format respectively.
- Multi-cloud virtual desktop assignments for Horizon Cloud pods on Microsoft Azure now support multiple tenant subnets from either the pod’s VNet or from multiple connected, peered VNets. (Feature debuted on February 23, 2021)
- Image Management Service for Horizon Cloud pods on Microsoft Azure is in Limited Availability. For more information and to request access to this feature, please email the VMware Horizon Cloud Service team at horizoncloudservice@vmware.com.
- Administrators can now generate Agent DCT logs from within the console for virtual desktop assignments and Farms on Horizon Cloud pods on Microsoft Azure. This feature is in Limited Availability. For more information, please email the VMware Horizon Cloud Service team at horizoncloudservice@vmware.com.
AppVolumes 2103 (4.4) Tools – Off line packaging for both AppVolumes On-Prem and on Azure
One of the great update from AppVolumes 2103 (aka 4.4) is now you can install only App Volumes Tools and package applications offline from a simple VM on VMware Workstation for example and produce the same package for App Volumes on Prem (.vmdk file) and for App Volumes on Azure (.vhd files). So exactly the same package for both environment.
So let me describe how I created my “Capture and Build” VM, how to capture and import your applications….
Continue reading…Adding Static Route to WS1 Access
I had a request from Spanish colleagues about adding static routes to Workspace One Access (in their case it was because of database in a different network).
I first had a look on our internal channel on Slack and find a first way to do it … but with Identity Manager version 3.3. However, when I try to test it in my Home Lab using my on-premise WS1 Access 20.10 it was totally different. vIDM 3.3 is based on Suse Linux when WS1 Access 20.10 is based on Photon 3. After some exchange by mail with my colleagues, they sent me the procedure they used for their deployment… different for the first two !!!
Yes they deployed Workspace One Access 20.01…
Basically both method work with vIDM 3.3 and Workspace One v20.01 as both are running Suse Linux
Method 1 : for Identity Manager 3.3 and WS1 Access 20.01: (thanks to Mahmood Ramzan for this one)
First edit “routes” files in /etc/sysconfig/network
vi /etc/sysconfig/network/routesThen add your route in this form : <net_range>/<mask> <gateway> <interface>
10.1.2.0/24 192.168.12.254 eth0Then restart your network and confirm the route is persistent:
# /etc/init.d/network restart
# ip route listMethod 2 : for Identity Manager 3.3 and WS1 Access 20.01: (thanks to Javier Perez for this one) :
After connecting to WS1 using sshuser and sudo as root (or direct login as root), create the ifroute-eth0 file
# vim /etc/sysconfig/network/ifroute-eth0 Add your route (same format as for vIDM 3.3)
and set permission on this file:
# chmod 644 /etc/sysconfig/network/ifroute-eth0Restart your network as explained above.
Method for Workspace One Access 20.10 and upward :
Starting with Workspace One Access 20.10, appliance are based on Photon 3.0. So adding a file call route-eth0 in /etc/sysconfig/network-scripts make it works by running /etc/sysconfig/network-scripts/ifup-routes but it doesn’t works when booting the appliance.
To add static routes to Photon appliance you need to follow this procedure :
So once logged as root edit this file : /usr/local/horizon/scripts/networkwizard.hzn
# vi /usr/local/horizon/scripts/networkwizard.hznFind the section “function save_sysconfig_properties” around line 800 (803 to be precise)
Alter the file to set the routes by adding the following lines in green :
function save_sysconfig_properties() {
if [ $ETHO_DEVICE_RESTORED -eq 0 ]; then
# any DHCP
local DHCP=no
if [ "$SYSCONF_IPV4_IP0" = "DHCP" -a "${SYSCONF_IPV6_IP[0]}" = "DHCP" ]; then
DHCP="yes"
elif [ "$SYSCONF_IPV4_IP0" = "DHCP" ]; then
DHCP="ipv4"
elif [ "${SYSCONF_IPV6_IP[0]}" = "DHCP" ]; then
DHCP="ipv6"
fi
echo save $ETH0_CONF
echo -n > $ETH0_CONF
echo "[Match]" >> $ETH0_CONF
echo "Name=eth0" >> $ETH0_CONF
echo "" >> $ETH0_CONF
echo "[Network]" >> $ETH0_CONF
echo "DHCP=$DHCP" >> $ETH0_CONF
if [ -n "$SYSCONF_IPV4_IP0" -a "$SYSCONF_IPV4_IP0" != "DHCP" ]; then
echo "Address=$SYSCONF_IPV4_IP0/`mask2cdr $SYSCONF_IPV4_NETMASK`" >> $ETH0_CONF
echo "Gateway=$SYSCONF_IPV4_GATEWAY" >> $ETH0_CONF
echo "DNS=$SYSCONF_NET_DNS" >> $ETH0_CONF
echo "LinkLocalAddressing=no" >> $ETH0_CONF
echo "IPv6AcceptRA=no" >> $ETH0_CONF
echo "[Route]" >> $ETH0_CONF
echo "Destination=10.0.0.0/24" >> $ETH0_CONF
echo "Gateway=192.168.0.250" >> $ETH0_CONF
echo "GatewayOnlink=true" >> $ETH0_CONF
fi
if [ -n "${SYSCONF_IPV6_IP[0]}" -a "${SYSCONF_IPV6_IP[0]}" != "DHCP" ]; then
local ndx=0
while true
do
local tmpip=${SYSCONF_IPV6_IP[$ndx]}
local tmppfx=${SYSCONF_IPV6_PFX[$ndx]}
if [ -z "$tmpip" ]; then
break
fi
echo "Address$ndx='$tmpip/$tmppfx'" >> $ETH0_CONF
ndx=$(($ndx + 1))
done
fi
fi
}
Reboot the appliance to ensure it works fine
App Volumes, load balancer health check
I recently had an issue with one of my App Volumes server: even if my server was down in an App Volumes point of view (connection lost the database), my Kemp load balancer see it up and running because: the web interface was up and favicon.ico was also available.
The template for App Volumes (part of Horizon 7 Template) is, in my opinion not complete and it missed the right way to configure health check
So the right way to configure load balancer ‘s health check is the following :
For Kemp :
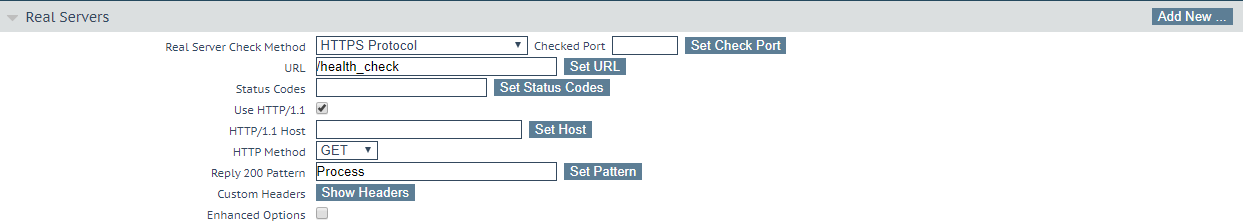
Guess who’s the only component not compatible with Windows Core ?
Ok so I made some test recently on installing VMware EUC components or Core version of Windows Server. It works with Horizon and App Volumes but I got information that installing Workspace One Access Connector on Core didn’t work as expected 🙂
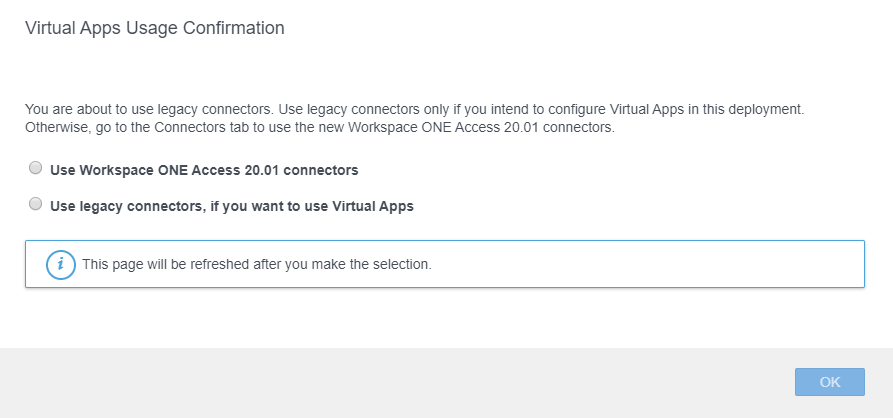
Revert Workspace One Access Connector to “Legacy”
With Workspace One Access 20.01 you have the choice to use the new Connector in version 20.01 as well or a Legacy connector ie. version 19.03 from the previous version of Workspace One Access.
Why 2 connectors ? because the latest version so 20.01 is unable to be used when you need to use “Virtual Apps”
Moving Workspace One Access database to a new MS SQL Server
I had to validate how to migrate WS1 Access database to another SQL Server.
This test concerns a dual-site configuration with 3 active nodes (R/W) on Site-A et 3 passive nodes on site B (R/O).
The first thing I did, was to set all nodes to passive (so read-only for all) so no more update will be done on the database.
After that I made a SQL backup of my database and copied it the new MS SQL Server.
VMware Horizon on Windows Server Core 2019
I recently have a customer requesting to install VMware Horizon on a Windows 2019 Core server. Most of customers prefer to have the “Desktop Experience” but for security reason some other prefer to limit to shell only interface.
Before installing VMware Horizon, ensure that all updates are applied to Windows 2019 Core (I had some strange behavior before doing that, like impossible to have the Flex Admin console or get “Login failed” on the new HTML 5 consoles)
The first main concern is getting signed certificate ready so Horizon will use it instead of its self signed certificate.
After copying the certificate in a local folder :
1 ) From the Administrator command prompt, type “powershell” to execute PowerShell command


Recent Comments