Horizon Suite 2212 is GA since last week and of course I already upgraded all my lab with this new release.
I was particularly interested by the Application on Demand so directly manage App Volumes application on RDS with all entitlement done within the Horizon Console.
The principle consist of adding App Volumes server in Horizon and then assign it to an “Automated” farm.
Now when you add you App Volumes Server into Horizon, you’ll certainly need to import App Volumes certificates into the “Trusted Root Certification Authorities” folder and then restart Horizon Services on all you Connection Servers.
Now even if doing that, you can encounter the following issue, with Enterprise signed certificate :
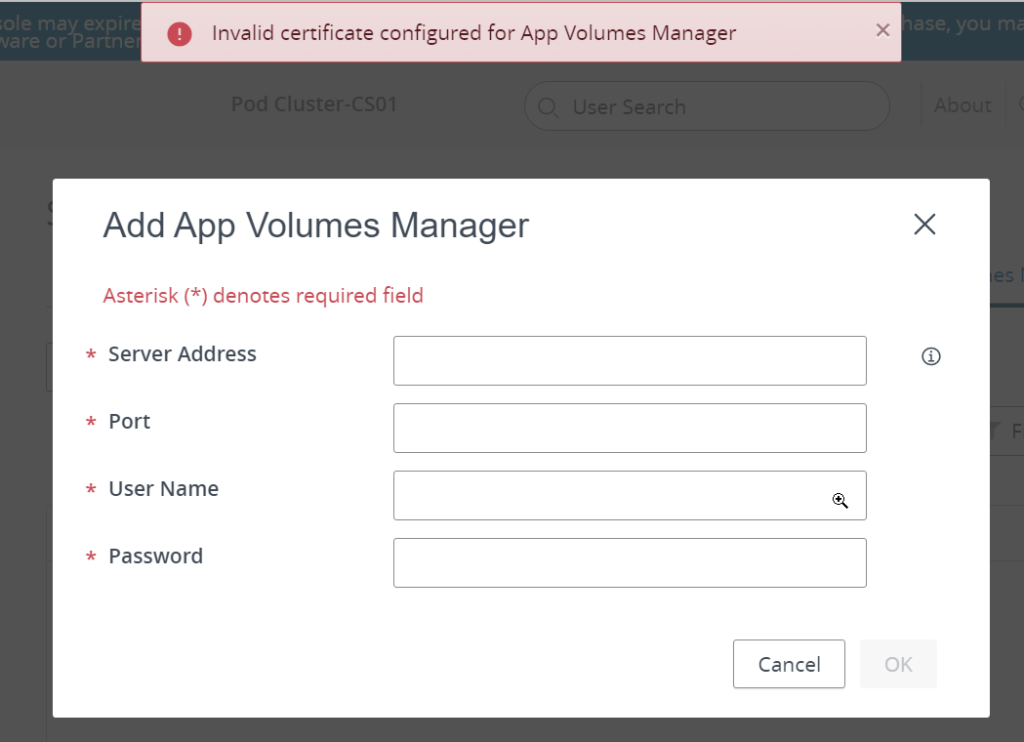
I had this issue on my lab, so to get it solved, I had to generate a new certificate for my App Volumes server using a new Template.
This is how to do it ….
Continue reading…

Recent Comments